
A new attack on Android devices that uses “Toast” notifications to help malware in gaining admin access or rights to Android’s Accessibility service has been reported by mobile security experts from Palo Alto Networks. This attack is often used to take over user’s Android devices. This isn’t new since for the past few years, most of the top Android malware makes use of the same technique to take control of user’s device.
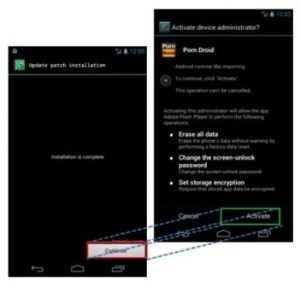
This technique involves tricking users during an installation of an app to grant it the permission to display or deliver content on top of other apps using the “Draw on top” permission. Once permission is given to the malicious apps, they take advantage of this by displaying intrusive pop-ups on the screen and ask users to confirm some message or to take some kind of action. When what’s really happening is that the app is requesting access to the Android Accessibility service and then use the “Draw on top” permission to deliver fake messages on top of the Activate button. The malicious apps would also use the same “Draw on top” tactic to deliver fake messages or contents on top of the pop-up used to grant the malware admin rights.
This kind of trick was known and used in live attack for approximately two years but was just recently explained in detail for the first time in a research paper entitled “Cloak & Dagger” which is a name that’s being used today to describe the attack’s routine entirely. Mobile security experts from Palo Alto stated that this research paper helped them in seeing other ways to carry out the Cloak & Dagger attacks. As they delve into this, it led them to Toast messages that are short-lived pop-ups which appears at the bottom of the screen. Many apps, as well as the Android OS use this notification to display self-fading messages. For instance, the ones that appears when Gmail confirms the sending of a message or when the user connects to a Wi-Fi network. The screenshot below is an example of a self-fading message.
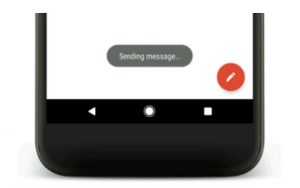
According to Palo Alto experts, these Toast messages can be used to carry out a variation of the Cloak & Dagger attack. Many attackers take advantage of Toast messages since they inherently appear above any apps and do not really require a malicious app to obtain the “Draw on top” permission during the installation process.
All the attackers have to do is to trick users into installing a malicious app on their device and then ask for admin access or rights to the Accessibility service but hides or masks the confirmation buttons and other description text with customized Toast messages. So instead of seeing an Activate button, attackers make use of Toast messages to make the button display “Continue”.
According to Christopher Budd, Senior Manager of Cybersecurity, “The Toast attack requires fewer explicit user steps to exploit and also can be exploited by apps that don’t come from Google Play. Taken together these make this vulnerability more broadly viable for possible attacks.”
Palo Alto researchers stated that all version of Android, except the Android 8.0 Oreo, are vulnerable to these kinds of overlay attacks. They also reported the issue to Google by the end of May, to which they responded by stating that requiring apps that use Toast messages to ask for the “Draw on top” permission just like everyone else.
This particular issue is tracked as CVE-2017-0752 was patched recently on Tuesday when Google released the September 2017 Android Security Bulletin. So it’s safe to say that all Android OS versions who had received the September 2017 security patch levels are safe from the Toast overlay attacks.
