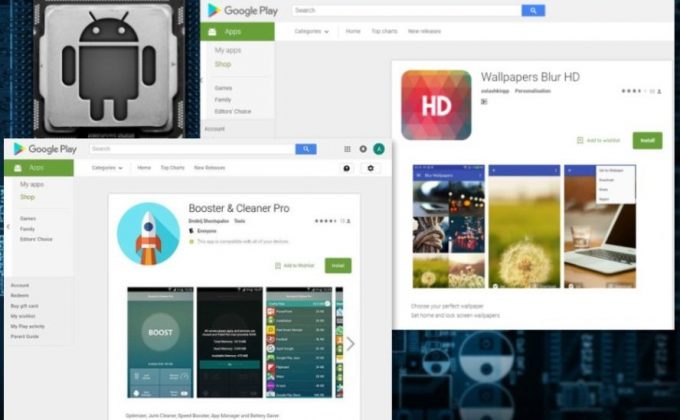
Recently, a new variant of Android ransomware has been spotted spreading through two apps in Google Play store which are “Wallpapers Blur HD” and “Booster Cleaner Pro”. Thankfully, these mobile malware can’t encrypt files. However, it threatens to leak sensitive information in the affected device if the user won’t be able to pay the ransom of $50 within 72 hours. This malware was discovered by the security researchers from McAfee’s mobile division.
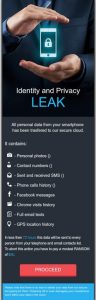
If you’re one of the unfortunate users who have been infected with LeakerLocker, then you must have found your device’s screen locked and you’ll notice a pop-up window as soon as one of the infected apps is downloaded. The message in the pop-up window states that the malware contains the information listed below and that all these information will be sent to each phone and email contacts if the payment won’t be sent in the given time frame. These are the information that the malware threatens to expose:
- Personal photos;
- Contact numbers;
- Sent and received messages;
- Phone call history;
- Facebook messages;
- Chrome visit history;
- Full email texts;
- GPS location history.
The cyber crooks behind LeakerLocker claims that all these information are transferred to their secure cloud. Meaning to say, even if you detected the malware in your device, it still won’t protect your personal files and data since it already stored them in their cloud.
According to researchers, the malware can access particular data by communicating with its Command and Control server. However, such threats aren’t proven to be true yet and it might just be a threatening tactic to get you to pay the ransom. In other words, no one really knows if it has the ability to copy your files and if they can even publish all these information and if they’ll be true to their words if you ever made the mistake of paying them.
Based on the two McAfee experts who analyzed the two infected apps, the ransomware does not really use any exploits and solely relies on the permission that users grant during the installation process. They also confirmed that LeakerLocker indeed has the ability to access data like email address, contacts, Chrome history, text messages, call history pictures and other device information. Nonetheless, even if it isn’t determined if this is just a scam, McAfee experts didn’t rule out the possibility that the malware could download module from its server to accomplish its threats if the user fails to pay the ransom.
The LeakerLocker makes its demands using a WebView component that it shows on all the apps in the device and then locks the device screen until the user pays the ransom. Hopeful for an immediate profit, the cyber crooks behind LeakerLocker only asks for $50 which can be paid through credit card transaction. Here’s the screenshot of LeakerLocker.
Way back in June, Chinese authorities arrested two individuals who were caught distributing Android ransomware after they processed the payment using traceable channels. And since the LeakerLocker group uses the same technique, there’s a big possibility that the authorities could track down the cyber criminals behind this ransomware.
