It seems like it was just yesterday that Apple promised users their devices were not affected by bugs, viruses, and other “PC problems”.
Those days are long in the past.
A recent vulnerability in iOS is so serious that the U.S. government weighed in on the matter. The vulnerability can be exploited using something called the Masque Attack, the American government said in an online bulletin posted at its Computer Emergency Readiness Team blog.
The vulnerability was discovered by a company called FireEye Inc., which claims that attacks have already been launched, including one specific campaign called WireLurker.
Here’s how this Masque Attack exploit works:
-The attack begins with the user installing an app from outside Apple’s App Store
-The app then runs the exploit on the device, giving the remote third party near-complete access to the iPhone
-Hackers could potentially use this exploit to steal login credentials like usernames and passwords
-Hackers could also remotely monitor activity on the device and access sensitive data stored on the iPhone or iPad
Apple is downplaying the vulnerability
Apple is understandably downplaying the issue. So far, the bug is only affecting users who install apps from outside the iTunes App Store.
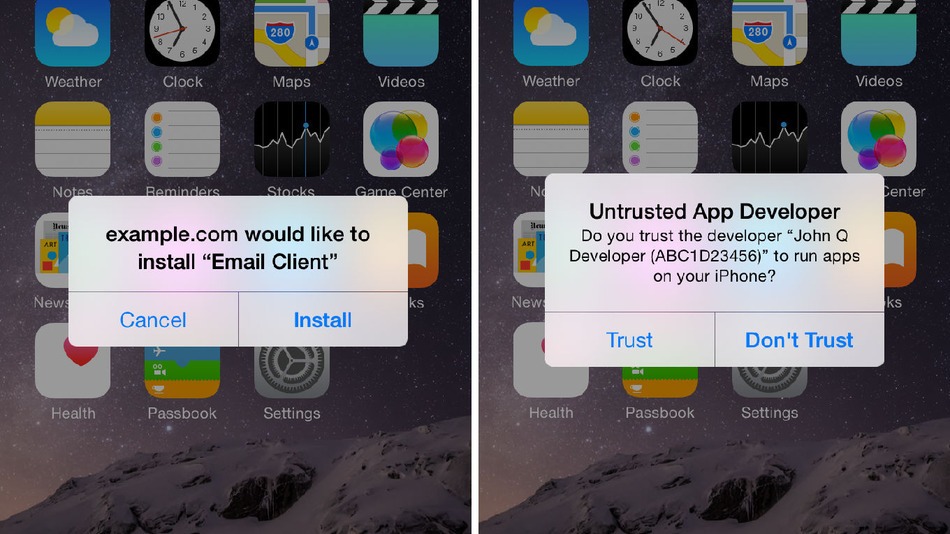
However, installing apps from outside the iTunes App Store isn’t as hard as some people think. Some websites and third-party apps deliver pop-ups which try to direct users to a download site for an app.
Users then have to click through various confirmation messages and warnings before installing the app. They need to click Install from the pop-up and then click Trust from the “Untrusted App Developer” warning box. However, it’s still a relatively easy path for a user to follow – especially if they’re uneducated about security threats.
The issue is currently affecting the majority of iPhones on the market today. Apple has not yet issued a response.
If you’re unfortunate enough to be affected by this attack, then you can read more information about solving the problem and avoiding future threats at FireEye’s official blog.